
Close


GhangorCloud is pleased to announce the release of Information Security Enforcer (ISE) 3.0. The updated version has full scale CASB features and new capabilities for controlling information being uploaded to cloud applications as well as a range of sophisticated reporting options for analyzing export of sensitive data to the cloud. Real time data leak prevention […]
See More
How do you know if your PII and HIPPA data is being used properly? Demonstrating compliance is a difficult task, unless you have evidence that your regulated information is being actively controlled. What would that look like?You could set up a control system whereby only people with the proper clearance could send or receive sensitive […]
See More
A malicious data leak involves a company employee or contractor who deliberately transports confidential information outside of the company for personal use. One of the key difficulties with insiders leaking information is that they are frequently entitled to use the information that they are taking. In order to stop insider leaks, you have to analyze […]
See More
If one of your employees was sending privately encrypted messages to people outside the company, would you need to know this? Would you want the ability to stop these messages? A Data Leak Prevention solution with advanced workflow will provide this capability.There are several kinds of workflows, depending on the level of security needed. A […]
See More
A military style command center puts all key facts and events together to allow for quick analysis of a situation. This is what security administrators require for management of the daily spectrum of DLP incidents. Some of the incidents are trivial, others will threaten the business. The key is to be able to sort them […]
See More
Health Care organizations collect and manage extremely sensitive information about individual patients and their practitioners. The information ranges from name and address to payment information and diagnoses. Since this is structured data, it is very easy to identify and target…
See More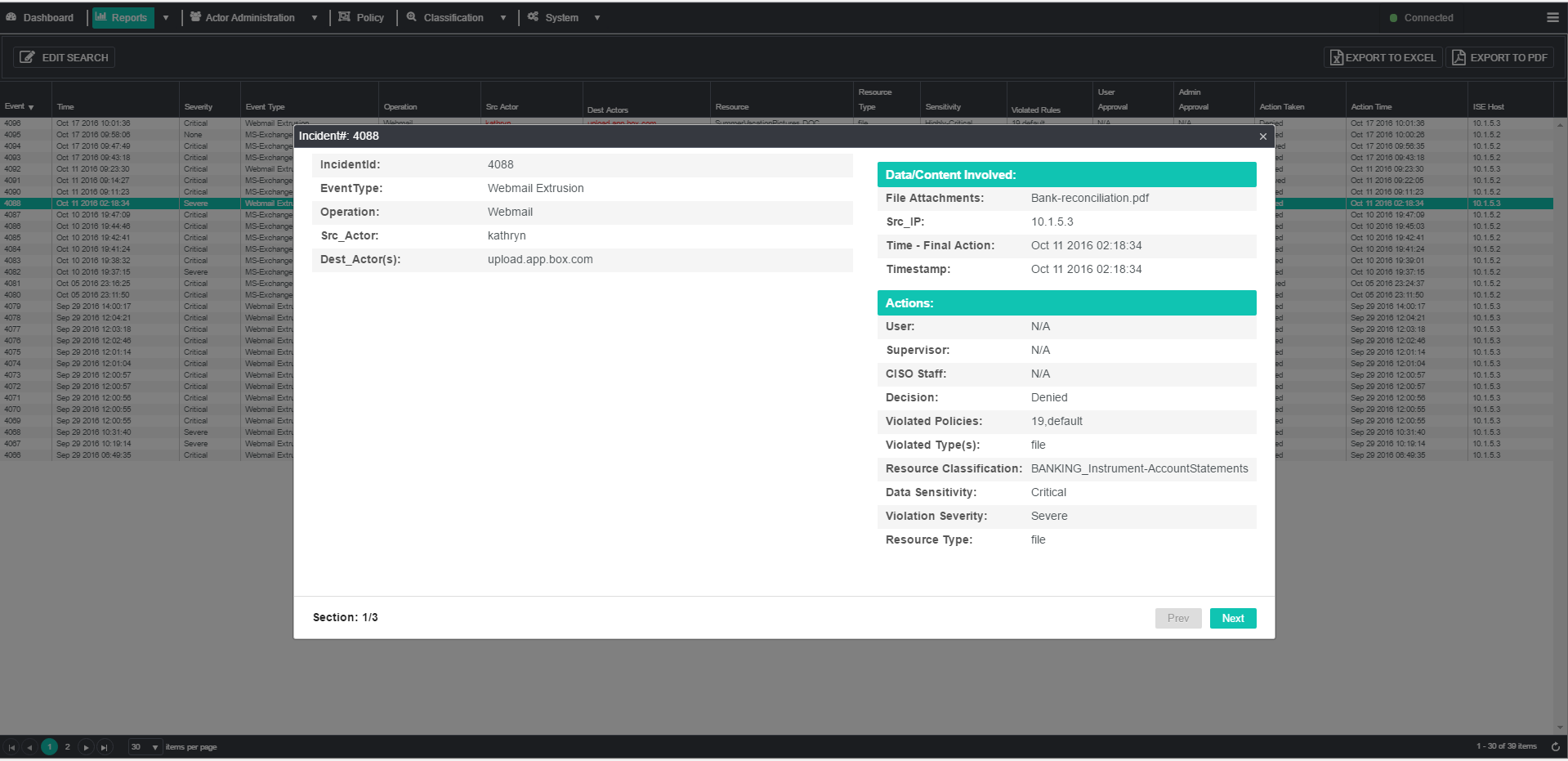
If you are lucky enough to be able to capture an attempted data leak, will you get all the facts you need about the attempt? What would a perfect incident report look like? Let’s start with the content of the…
See More
If you have a Data Leak Prevention system from one of the traditional providers, you have the opportunity to constantly play tag. In order to ensure the safety of your sensitive documents, you must constantly identify and find all the…
See More
A key strategy for managing information security is to ensure that sensitive information is only touched by people who have responsibility for that information. When you want to prevent sensitive data leaks, one of the first things to analyze is…
See More
Policies are the core of Data Leak Prevention systems. Unfortunately, one of the weaknesses of all major DLP systems is the manual nature of policy creation. It requires that the person creating policy understands every kind of content and every…
See More
The first generation In the beginning, companies did not think about data leakage. They thought about document control. This was a natural outgrowth of authoring tools and document management systems. The key concepts of this phase were about password protection…
See MoreGet started by completing the form below
We will get back to you soon