Is there a perfect incident report for an attempted data leak?
If you are lucky enough to be able to capture an attempted data leak, will you get all the facts you need about the attempt? What would a perfect incident report look like?
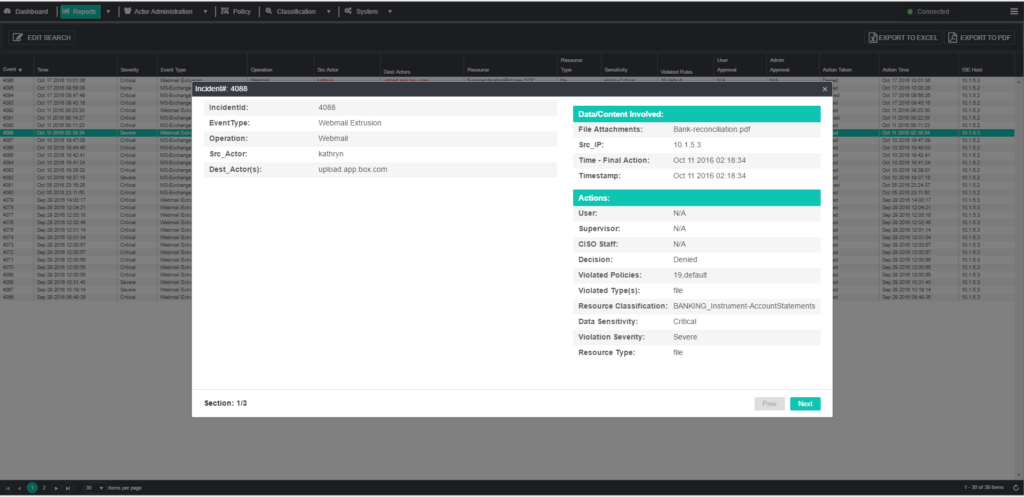
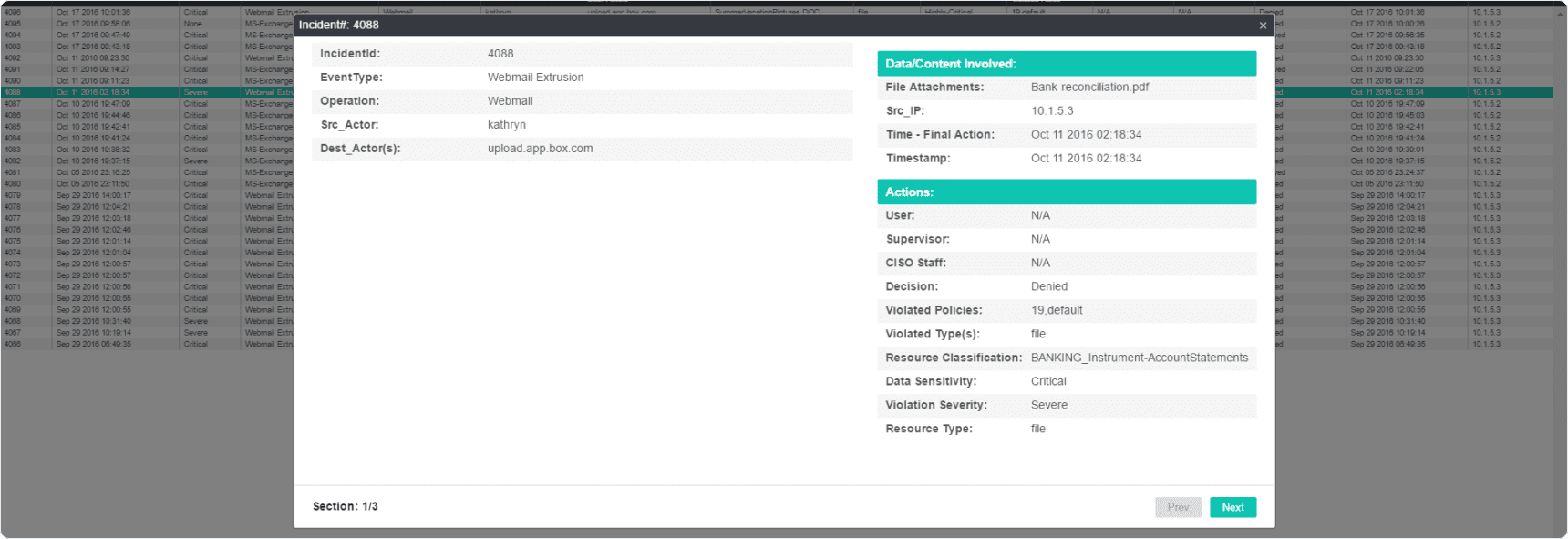
Let’s start with the content of the attempted leak. How do you know what kind of sensitive data was involved? You would have to inspect and classify the data so that it could be properly categorized. It could be one of many different kinds of sensitive data – customer information, credit card numbers, HIPPA data. Some kinds of data are more sensitive than others. It would be very helpful to be able to look at attempted leaks by prioritizing the level of importance that data has to the company.
Classification requires an analysis of content that compares any kind of payload with multiple categories of sensitive documents. And if the classification engine is really good, it labels those potential leaks as Financial Document, Legal Document, etc. It might even tell you the level of sensitivity – critical vs severe. And just so you can really check, it would save the content along with the other information about the leak.
So what else do you need? Name of the person sending the content? That would really help. But what if the sender was allowed to have sensitive information? Maybe the problem is in who would be receiving the information? Or where it was going. That would be needed also. And that would require that you have information about the policy that was applied during the incident. You might need to look that up to make sure there is no false positive involved.
list of data for a perfect incident report:
- From who to whom
- What type of information
- How was the information transmitted – email, web app
- What severity
- What policy was invoked
- Action taken – allow, block, refer to supervisor
- When did the incident occur
Having this complete list of information would give you a comprehensive forensic trail for even the most rigorous compliance review.
Wouldn’t it be great if all of this information was in one place so that you didn’t have to gather data from multiple places to get it?
Maybe a perfect incident report would look something like this: