
Close

Let us show you how GhangorCloud’s pioneering 4th Generation DLEP technology

Real-time Centralized Command Control Collaboration & Intelligence System for the Enterprise & Cloud SOCs
Industry’s First and Only Identity & Role driven Access Control for each type and class of Information & Data Elements
Information Governance & Regulatory Compliance with Segmentation of Duty (SoD) based Controlled Access and Use of Applications, Protocols, Contents and Information
Fully Integrated Automatic Access Control to Web Applications, Services, Content and Information
Industry’s Most Advanced Auto-Identification and Auto-Classification Engine
Industry’s Best Real-Time High Granularity Automated Policy Synthesis and Enforcement
4th GENERATION —
A holistic approach to information security & compliance
Information Security Enforcer (ISE™) redefines industry’s standard of Information Security &
Compliance.
Widely recognized in the industry as the Most Advanced Data Leak
Exfiltration Prevention Platform for within the Enterprise and the Web information security.
Transparently fitting into the Enterprise & Cloud infrastructure, Information Security Enforcer (ISE™) seamlessly integrates DLEP and CASB features thus providing the most comprehensive protection against data exfiltration and extrusion.
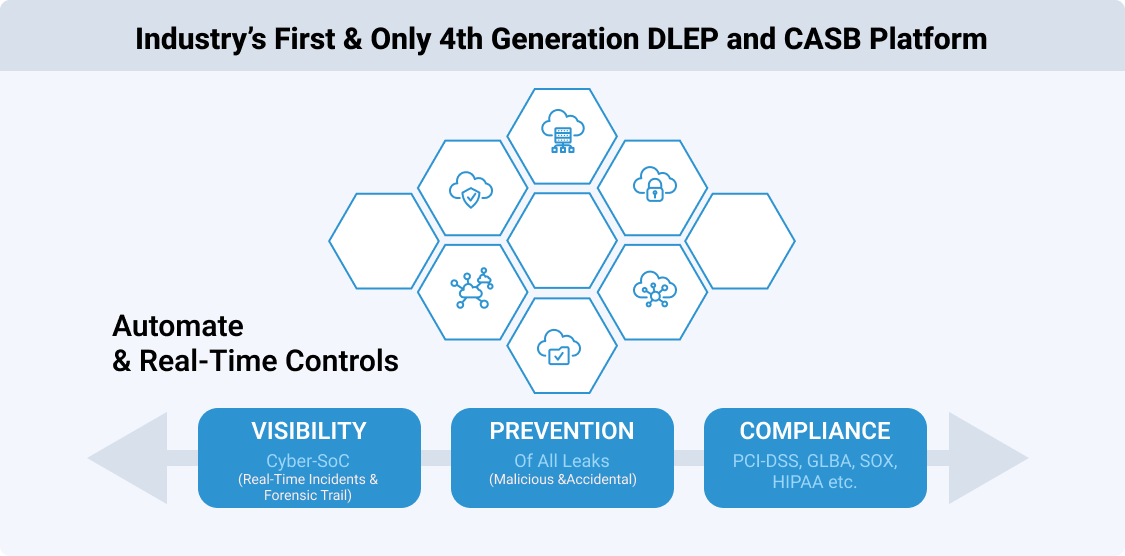
Information Security Enforcer (ISE™) is “Industry’s First and Only” solution that seamlessly addresses both Malicious and Inadvertent data exfiltration or theft via any Channel, Protocol or Web Service.

Sophisticated Artificial Intelligence (AI) based platform for “Total Automation” of Complex and Error Prone Tasks
CyberSOC for the Enterprise & Cloud Centralized Command Control & Intelligence System for the Enterprise & Cloud SOCs


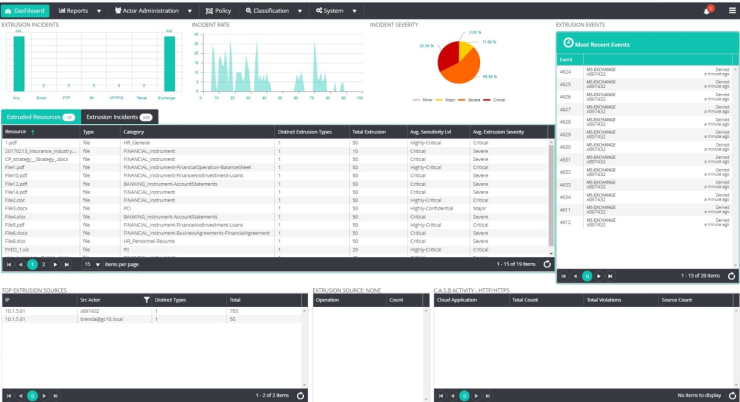

A military style command center puts all key facts and events together to allow for quick analysis of a situation. This is what security administrators require for management of the daily spectrum of DLP incidents. Some of the incidents are trivial, others will threaten the business. The key is to be able to sort them […]
See More
If one of your employees was sending privately encrypted messages to people outside the company, would you need to know this? Would you want the ability to stop these messages? A Data Leak Prevention solution with advanced workflow will provide this capability.There are several kinds of workflows, depending on the level of security needed. A […]
See More
A key strategy for managing information security is to ensure that sensitive information is only touched by people who have responsibility for that information. When you want to prevent sensitive data leaks, one of the first things to analyze is…
See More
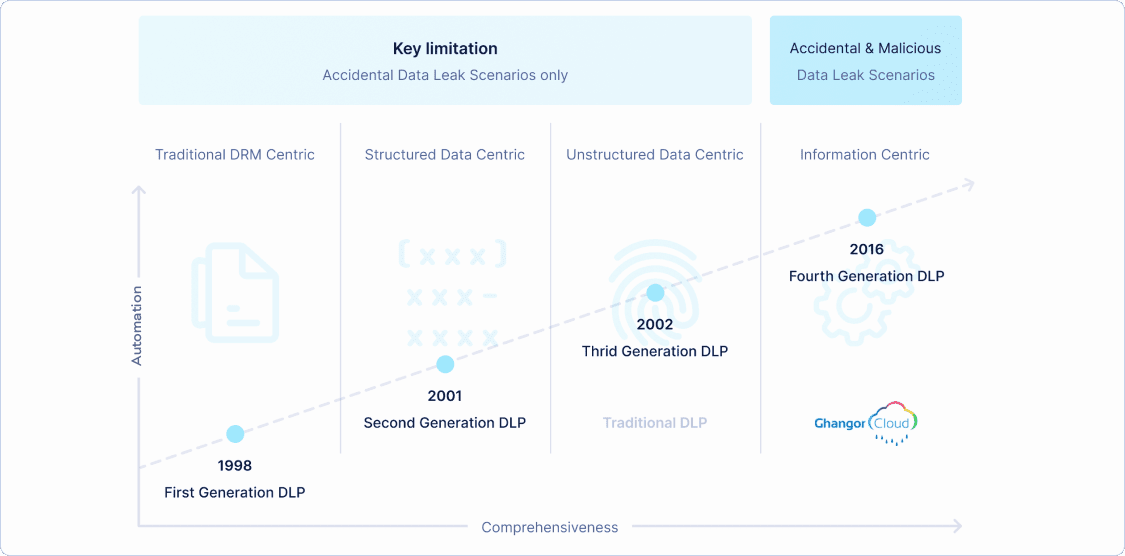
The first generation In the beginning, companies did not think about data leakage. They thought about document control. This was a natural outgrowth of authoring tools and document management systems. The key concepts of this phase were about password protection…
See MoreGet started by completing the form below
We will get back to you soon